AsyncRAT v0.5.6 with Source
In the digital age, where connectivity is ubiquitous, threats lurk in the shadows of the internet, waiting to infiltrate unsuspecting systems. One such menace that has recently gained notoriety is AsyncRAT, a remote access trojan (RAT) that poses a significant risk to individuals, businesses, and organizations worldwide. Asynchronous Remote Administration Tool, commonly known as AsyncRAT, has emerged as a potent weapon in the arsenal of cybercriminals, enabling them to compromise systems, steal sensitive data, and wreak havoc with impunity.
Understanding AsyncRAT v0.5.6:
AsyncRAT v0.5.6 is a type of malware designed to provide cybercriminals with unauthorized remote access to compromised systems. What sets AsyncRAT v0.5.6 apart from conventional malware is its asynchronous nature, allowing it to execute multiple tasks simultaneously without waiting for each task to complete before starting the next one. This capability enhances its efficiency and stealth, making it harder to detect and mitigate.
Functionality and Capabilities AsyncRAT v0.5.6:
The primary objective of AsyncRAT is to gain unauthorized access to a victim’s system, giving cybercriminals complete control over the infected device. Once installed on a target system, AsyncRAT can perform a wide range of malicious activities, including:
- Remote Access: Cybercriminals can remotely control the infected system, execute commands, and manipulate files and processes without the user’s knowledge.
- Keylogging: AsyncRAT can log keystrokes, enabling cybercriminals to capture sensitive information such as login credentials, financial data, and personal messages.
- Surveillance: The malware can capture screenshots and record audio and video from the victim’s device, compromising their privacy.
- Data Theft: AsyncRAT can exfiltrate sensitive data stored on the infected system, including documents, images, and passwords.
- Distributed Denial of Service (DDoS): In some cases, AsyncRAT may be used to launch DDoS attacks by leveraging the compromised devices to flood target servers with malicious traffic, causing them to become inaccessible to legitimate users.
Distribution and Infection Vectors:
AsyncRAT is typically distributed through various means, including phishing emails, malicious websites, and software downloads from untrusted sources. Once a victim inadvertently executes the malware on their system, it can evade detection by exploiting vulnerabilities in the operating system or security software.
Evading Detection and Mitigation:
AsyncRAT employs various techniques to evade detection by antivirus and security solutions, including obfuscation, encryption, and polymorphism. Moreover, its ability to operate asynchronously makes it challenging for traditional security measures to detect and block its malicious activities effectively.
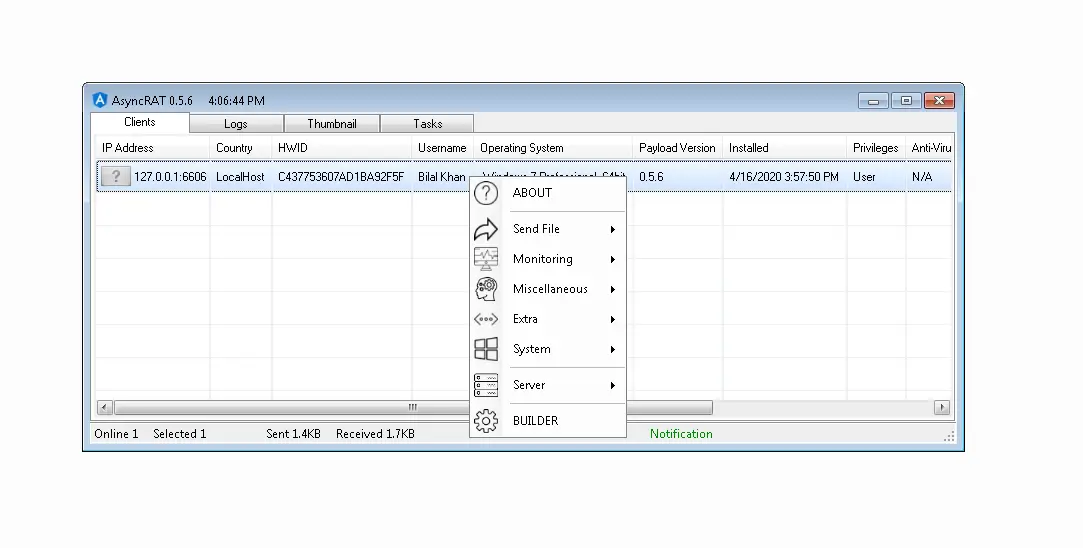
Send File
To Memery
To Disk
Monitoring
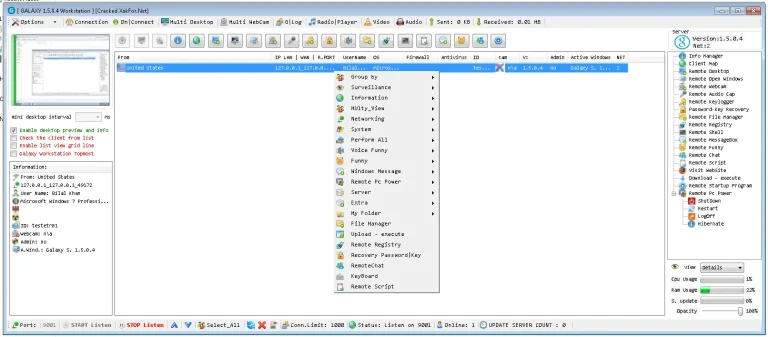
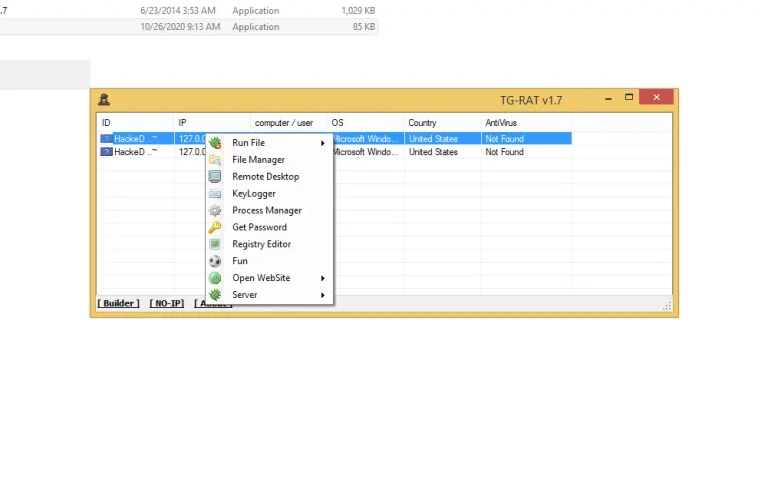
Remote Desktop
File Manager
Process Manager
Report window
Webcam
Bot Killer
USB Spread
Seed Torrent
Remote Shell
DOS Attack
Execute.NetCode
Extra
Visit Website
Send Message BOX
Chat
Get Admin Rights
Blank Screen
Disable windows defender
Log Off
Restart
ShutDown