Lordix botnet 2025 Cracked
The Lordix botnet 2025 Cracked , also referred to as L0rdix in some sources, is a sophisticated and versatile malware that emerged around 2018 as a powerful tool for cybercriminals targeting Windows-based systems. Designed with a modular architecture, Lordix combines data theft, cryptocurrency mining, and botnet capabilities, making it a formidable threat in the cybersecurity landscape. This essay explores the origins, functionalities, infection mechanisms, and mitigation strategies associated with the Lordix botnet, shedding light on its impact and the challenges it poses to cybersecurity professionals.
Origins and Development
Lordix botnet 2025 Cracked first gained attention in 2018 when cybersecurity researchers, such as Ben Hunter from enSilo, reported its availability for purchase on underground dark web forums. Written in .NET, Lordix is a multi-purpose attack tool still considered to be in the development phase during its initial discovery, with indicators suggesting that its creators were actively refining its capabilities. The malware is obfuscated using tools like ConfuserEx and, in some cases, the more advanced .NETGuard, which enhances its ability to evade detection by security software. Its design reflects a deliberate effort to create a “Swiss Army knife” for Windows hacking, combining multiple malicious functionalities into a single package.

The malware’s development trajectory indicates an intent to cater to cybercriminals seeking a comprehensive tool for various illicit activities. While some of its modules, such as encryption and data handling, were initially described as rudimentary, the ongoing development suggested potential for more sophisticated iterations. Lordix’s availability on dark web marketplaces, often accompanied by cracked versions and tutorials, further democratized its use, enabling even less experienced attackers to deploy it effectively.
Functionalities of Lordix botnet 2025 Cracked
Lordix botnet 2025 Cracked is distinguished by its modular structure, which allows it to perform a wide range of malicious activities. Its core capabilities include:
-
Data Theft (Stealer Module): Lordix is equipped with a “Stiller” module that extracts sensitive information from infected systems. This includes browser data such as cookies, saved passwords, and user preferences from supported web browsers. The malware can also retrieve files from specified folders and subfolders, with configurable extensions, and send them to a command-and-control (C2) server. This capability makes Lordix a potent tool for stealing personal and financial information, which can be used for identity theft or sold on underground markets.
-
Cryptocurrency Mining (Miner Module): The malware includes a module for cryptocurrency mining, leveraging the infected system’s resources to mine digital currencies. Lordix optimizes its mining operations by collecting performance metrics from the victim’s PC, ensuring efficient resource utilization. It can also hijack existing cryptocurrency wallet files, further increasing its profitability for attackers.

-
Botnet Operations: Lordix can enslave infected computers, turning them into bots within a larger botnet network. This allows attackers to orchestrate coordinated attacks, such as Distributed Denial-of-Service (DDoS) campaigns, by flooding targeted domains with traffic. The botnet functionality also supports remote command execution, enabling attackers to upload and execute additional payloads, open specific URLs, or terminate processes on the infected system.
-
Clipper Module: This module targets cryptocurrency transactions by monitoring and altering clipboard content. For instance, it can replace a victim’s cryptocurrency wallet address with one controlled by the attacker, redirecting funds to the cybercriminal’s account. The module’s configuration can be adjusted via the C2 panel, allowing attackers to target multiple wallet types across independent branches.
-
Persistence and Propagation: Lordix employs several techniques to maintain persistence on infected systems. It copies itself to traditional locations, such as scheduled tasks, to ensure it remains active even after system reboots. Additionally, Lordix can infect removable drives, such as USB devices, by hiding legitimate files and directories and mapping itself to their icons. This deceptive tactic increases the likelihood of the malware spreading to other systems when users access the infected drives.
-
Anti-Detection Mechanisms: Lordix is designed to evade detection by antivirus programs and malware analysis tools. It performs checks for virtual environments and sandboxes commonly used by researchers, such as VirtualBox, VMware, Sandboxie, and others. By querying Windows Management Instrumentation (WMI) and registry keys, Lordix can detect the presence of analysis tools like Wireshark or OllyDbg and terminate its operations to avoid exposure. This anti-analysis capability makes it challenging for security researchers to study and counteract the malware.
Infection Mechanisms
Lordix typically spreads through opportunistic scanning of vulnerable systems rather than targeting specific individuals or organizations. It exploits common vulnerabilities, such as outdated operating systems or open firewalls, to infiltrate Windows-based machines. Once a system is compromised, Lordix communicates with its C2 server to transmit collected data and receive updated configurations or commands. The malware’s ability to infect removable drives further amplifies its reach, as users inadvertently spread it by connecting infected USB devices to other machines.
The botnet recruitment process is semi-automated, allowing attackers to build large networks of infected devices. This scalability makes Lordix particularly effective for large-scale attacks, such as DDoS campaigns or widespread data theft operations. Its peer-to-peer (P2P) communication capabilities, noted in some botnet architectures, enhance its resilience by eliminating reliance on a single C2 server, making it harder for law enforcement to disrupt.
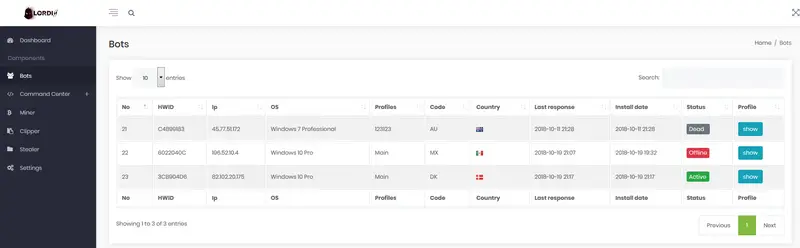
Feature of Lordix botnet 2025 Cracked
3.loading and starting (to disk)
4. Update client on PC and invisible)
6. Zack7.Command execution
8. Uploading a file to the server
9. Http ddos (beta)
11.Targeting by system Miner module:
12.Minin on the PC user profile
15. hashrate display Stiller module: cookies and passes from browsers files’
floor (in folders and subfolders extension can be configured in the panel)
sticks in the panel
Clipper module:
benefits in the text
fertilizerinto the panel
wallets can be configured from the panel
in 3 independent branches , if only to remove the most
be with another
USb auto
22.zae.
ead
there are no drops, all work happens 1 file
4.0
Virtual machine protection
Spoiler: List
– VirtualBox
– VMWare
– Anubis
– OllyDBG
– Sandboxie
– Mawr
– Procexp
– Wine.
– apateDNS
– Wireshark