Predator Pain Keylogger v13
What is Predator Pain Keylogger v13?
Predator Pain v13 is a software-based keylogger, a type of surveillance tool designed to record keystrokes on a victim’s computer. Unlike hardware keyloggers, which require physical access, Predator Pain can be installed remotely, often as part of a remote administration Trojan (RAT) or rootkit. It is typically acquired through underground forums and has been noted for its ease of use, requiring minimal technical expertise to deploy. The software is compatible with all Windows operating systems and requires Microsoft .NET Framework 4.0 or higher to function properly.
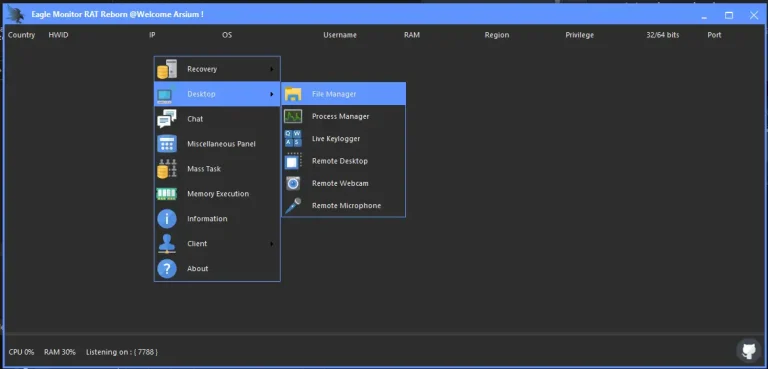
The keylogger is part of a broader malware toolkit that goes beyond simple keystroke logging. It includes features such as browser credential dumping, email client data theft, display capture, and exfiltration of stolen data via email, FTP, or PHP-based web panels. These capabilities make it a versatile tool for cybercriminals targeting both individuals and small to medium-sized businesses (SMBs).
Key Features of Predator Pain v13
Predator Pain v13 is equipped with a range of malicious functionalities, making it a significant threat. Below are its primary features, based on analyses from cybersecurity sources:
-
Keylogging: Captures every keystroke, including sensitive information like passwords, banking details, and personal messages, with awareness of the active window or process.
-
Credential Theft: Extracts cached credentials from web browsers (e.g., Firefox, Chrome, Opera, Internet Explorer), email clients (e.g., Outlook), and messaging platforms (e.g., AIM, Pidgin, Trillian).
-
File and Data Stealing: Targets specific data, including Bitcoin wallets, Minecraft accounts, Runescape pins, and files from FTP clients like FileZilla and FTP Commander.
-
Screen and Clipboard Logging: Takes screenshots and logs clipboard content, providing cybercriminals with visual and contextual data.
-
System Information Gathering: Collects details about the victim’s system, including installed software, operating system version, and CD keys.
-
Evasion Techniques: Disables critical system tools like Task Manager, Command Prompt, Registry Editor, and System Configuration to avoid detection and removal.
-
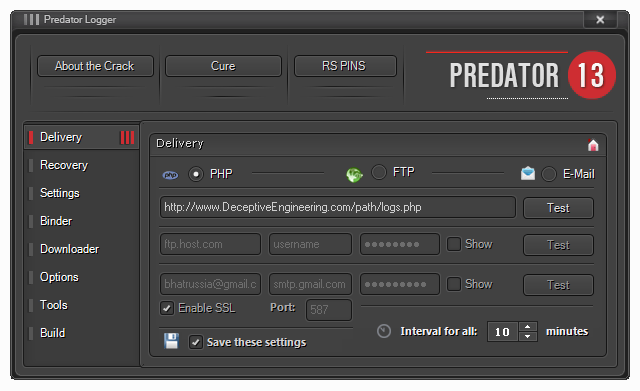
Data Exfiltration: Sends stolen data to attackers via email, FTP, or PHP-based web panels, with configurable intervals for log delivery.
-
Additional Features: Supports USB and P2P spreading, adds itself to startup for persistence, and includes capabilities like URL visiting, file cloning, and icon support for disguising malicious files.
These features make Predator Pain v13 a “big thief,” capable of compromising a wide range of sensitive information, as noted in malware analysis reports.
Support
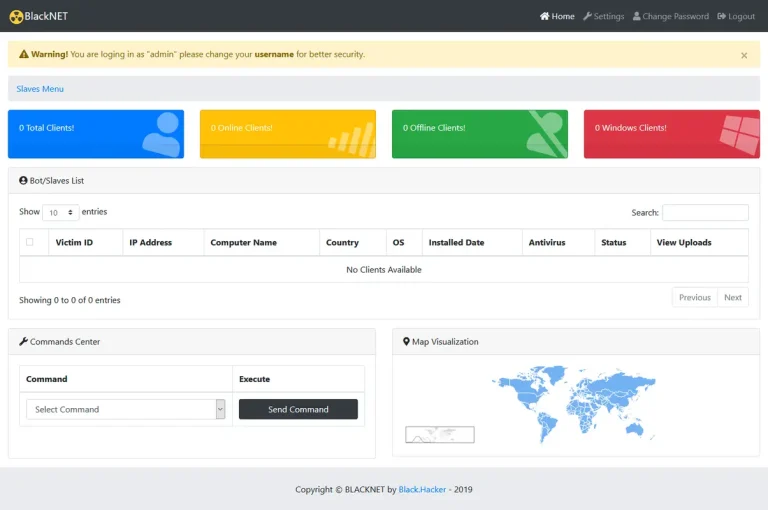
PHP Panel
Ftp
Email
Stealrs
Minecraf
bitcoin wallet
runescape pins
rsbot recovery
epic bot recovery
rarebot recovery
IMVU
NO IP
AIM
Pidgin
Trillian
Filezila
Sysytem info
IDM
Paltal
Nimbuzz
DyDNS
Jdownloader
Flash XP
Core ftp
Smart ftp
win key
Firefox
Chrome
Opera
Safar
Internet explorer
outlook
cd keys
Ftp Commander
Keyloggins
Clear Steam
Melt
Usb Spread
P2p Spread
Add start up
disable regedit
Clipboard loggin
Disable cmd
Screen shot
Clear data
disable msconfig
Run email confirmation
delay execution
disable task manager
multi downloader
url visitor
File cloner
icon support
2: Fill your mail.com account username and password
3: Change the SMPT to the one i have on, Do not mess with the port.
4: Set your time interval to how much time after you want the logs ( Recommended to make a long time for more results )