SpyEye Botnet 2025
The SpyEye botnet, a notorious banking Trojan that emerged in 2009, has left a significant mark on the cybersecurity landscape. Known for its sophisticated design and ability to steal financial credentials, SpyEye was a dominant force in cybercrime during its peak. While its primary developers, Aleksandr Andreevich Panin and Hamza Bendelladj, were sentenced in 2016, the botnet’s legacy persists, with occasional references to updated versions appearing in underground forums. This article explores the historical context of SpyEye, its technical evolution, and its relevance in 2025, drawing on recent discussions and the broader botnet threat landscape.
Historical Context
SpyEye was a third-generation botnet, succeeding the infamous Zeus Trojan. It targeted online financial transactions, primarily banks, using techniques like keystroke logging, form grabbing, and web injections to steal credentials. Sold on underground forums for $500–$8,500, SpyEye was accessible to cybercriminals, enabling widespread attacks. By 2012, it had infected over 1.4 million computers, compromised 100,000 bank accounts, and caused nearly $1 billion in losses globally.
The botnet’s success stemmed from its modular design, including a Bot Development Kit (BDK), plugin architecture, and web-based Command and Control (C&C) system. These features allowed operators to customize attacks and evade detection. A notable case was the hacker “Soldier,” who netted $3.2 million in six months using SpyEye to command a 25,000-computer botnet.
Legal efforts culminated in 2016 when Panin received 9.5 years and Bendelladj 15 years in prison for their roles in developing and distributing SpyEye. Despite these convictions, the botnet’s code and techniques influenced subsequent malware, and discussions about updated versions, like SpyEye 1.3.48, surfaced as recently as 2024.
Technical Evolution
SpyEye’s architecture was advanced for its time, leveraging HTTP-based C&C communication to blend with legitimate traffic, making detection challenging. Its plugins, such as those for DDoS attacks, remote desktop protocol (RDP), and custom web injections, enhanced its versatility. For instance, the form grabber feature stole sensitive data like 3D Secure passwords, while web injections tricked users into entering credentials on fake login pages.
By 2011, SpyEye incorporated Zeus’s source code, merging features to create a hybrid botnet. Updates like version 1.3.4.x improved security by storing binaries in MySQL databases as binary large objects (BLOBs) and restricting uploads to .EXE and .BIN files to patch vulnerabilities. These changes reflected a shift toward resilience against takedown efforts and researcher scrutiny.
In 2024, a post on blackhatrussia.com advertised SpyEye 1.3.48, claiming compatibility with modern browsers like Firefox 13 and Internet Explorer, along with new injects and plugins. While this suggests ongoing maintenance, the post’s credibility is uncertain, and it may reflect niche activity rather than a widespread resurgence. The botnet’s core techniques—keystroke logging, form grabbing, and phishing-style attacks—remain relevant but are now common in newer malware.
SpyEye in 2025: Current Relevance
As of 2025, SpyEye itself is not a dominant threat. The botnet landscape has shifted toward IoT-based botnets, like Mirai variants, which exploit the growing number of connected devices (projected to reach 75.44 billion by 2025). These botnets prioritize Distributed Denial-of-Service (DDoS) attacks and crypto-jacking over financial theft. However, SpyEye’s techniques have been absorbed into modern banking Trojans and crimeware kits, perpetuating its influence.
Recent analyses, such as a 2024 ResearchGate paper, highlight SpyEye’s role as a case study for third-generation botnets, emphasizing its modular design and economic motivations. Its ability to target sensitive data aligns with current trends in cybercrime, where financial gain remains a primary driver. Nonetheless, advanced detection techniques, including machine learning models trained on datasets like N-BaIoT, have improved the identification of HTTP-based botnets, reducing the effectiveness of SpyEye-like malware.
Underground forums occasionally mention SpyEye, but these discussions likely involve legacy code or repackaged versions rather than a revived botnet. The high-profile arrests of its creators and the takedown of its infrastructure by Microsoft and other entities in 2012 weakened its ecosystem. Modern cybercriminals favor newer tools with better obfuscation and scal
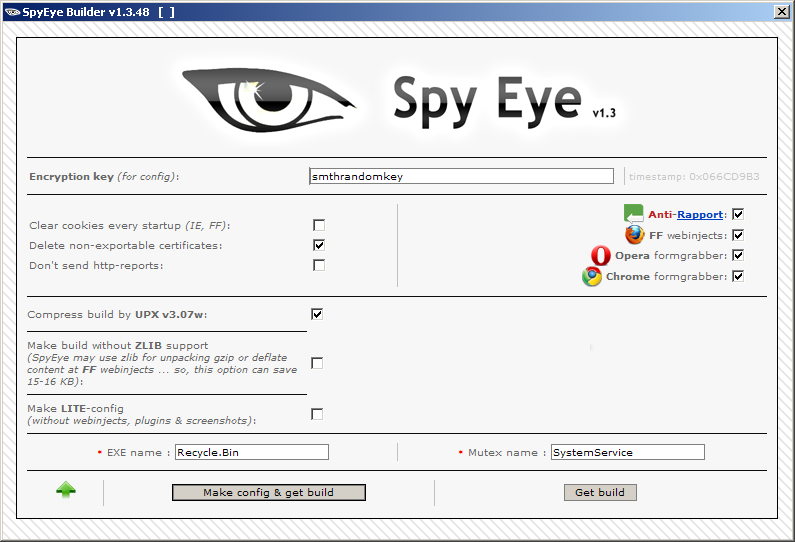
Spy Eye version 1.3.48 is private and more updated, this version will work and inject Firefox 13 (latest) and Internet Explorer
Need get full installation and your binary for speeding, you also have discounts on new injects and one free re installation
Once victim is infected, bot will inject fake browser content inside website like a form, once they fill in the form you get their data
Form grabber is unique spy eye feature that allows you to steal form post data like VBV or MasterCard 3D passwords, as well as liberty reserve pins and login)
This includes all the newest software for:
[+] Admin Panel
[+] Formgrabber Panel
[+] Gate Installer
[+] Back Connect
[+] Collector
[+] Anti-Rapport (Anti-Thrusteer)
Injection types:
[+] Internet Explorer
[+] FireFox
[+] Google Chrome
[+] Opera
Plugins:
[+] Custom Connector (to avoid that your admin panel is being tracked by Spyeyetracker)
[+] Webfakes
[+] RDP
[+] DDOS
[+] Block
[+] Billinghammer
[+] USB-Spread
[+] Socks5 Back Connect
[+] FTP Back Connect
[+] Bugreport
[+] CC-Grabber or
[+] Creditgrabber
[+] FFcertificate grabber
[+] SpySpread